Preparing for the rollover with bind and it’s DNSSEC policies
Make sure you have at least bind 9.16.0, because otherwise the policies are not available. To be able to use bind’s DNSSEC-policy feature first the current setup has to be migrated to a policy. The original setup was the following:
zone "t0d.nl" {
...
auto-dnssec maintain;
inline-signing yes;
...
};
And I converted this to the following custom policy :
dnssec-policy "rsa_default" {
dnskey-ttl 24h;
keys {
ksk lifetime unlimited algorithm RSASHA256 2560;
zsk lifetime 90d algorithm RSASHA256 1536;
};
max-zone-ttl 3600;
parent-ds-ttl 600;
parent-propagation-delay 2d;
publish-safety 14d;
retire-safety 14d;
signatures-refresh 5d;
signatures-validity 15d;
signatures-validity-dnskey 15d;
zone-propagation-delay 2h;
};
And then using that policy on the zone definition.
zone "t0d.nl" {
type master;
dnssec-policy rsa_default;
//auto-dnssec maintain;
//inline-signing yes;
...
};
New policies for the rollover and the future
During the rollover I need to have both algorithms in the zone, so I created two extra policies.
dnssec-policy "rsa_to_ecdsa" {
keys {
ksk lifetime unlimited algorithm RSASHA256 2560;
zsk lifetime 90d algorithm RSASHA256 1536;
ksk lifetime unlimited algorithm ECDSAP256SHA256;
zsk lifetime 90d algorithm ECDSAP256SHA256;
};
dnskey-ttl 24h;
max-zone-ttl 3600;
parent-ds-ttl 600;
parent-propagation-delay 2d;
publish-safety 14d;
retire-safety 14d;
signatures-refresh 5d;
signatures-validity 15d;
signatures-validity-dnskey 15d;
zone-propagation-delay 2h;
};
dnssec-policy "ecdsa256_default" {
keys {
ksk lifetime unlimited algorithm ECDSAP256SHA256;
zsk lifetime 90d algorithm ECDSAP256SHA256;
};
dnskey-ttl 24h;
max-zone-ttl 3600;
parent-ds-ttl 600;
parent-propagation-delay 2d;
publish-safety 14d;
retire-safety 14d;
signatures-refresh 5d;
signatures-validity 15d;
signatures-validity-dnskey 15d;
zone-propagation-delay 2h;
};
So I will use the rsa_to_ecdsa policy during the rollover and when that is
working I will use the ecdsa256_default as a final policy.
Doing the DNSSEC algorithm rollover
To start the rollover I changed the policy on t0d.nl to rsa_to_ecdsa.
zone "t0d.nl" {
type master;
dnssec-policy rsa_to_ecdsa;
...
};
After that was done bind needed to know there was a new config available, so I reload the config.
[root@amys ~]# rndc reconfig
This will result in 2 KSK’s and 2 ZSK’s in the zone, as shown in the following picture:
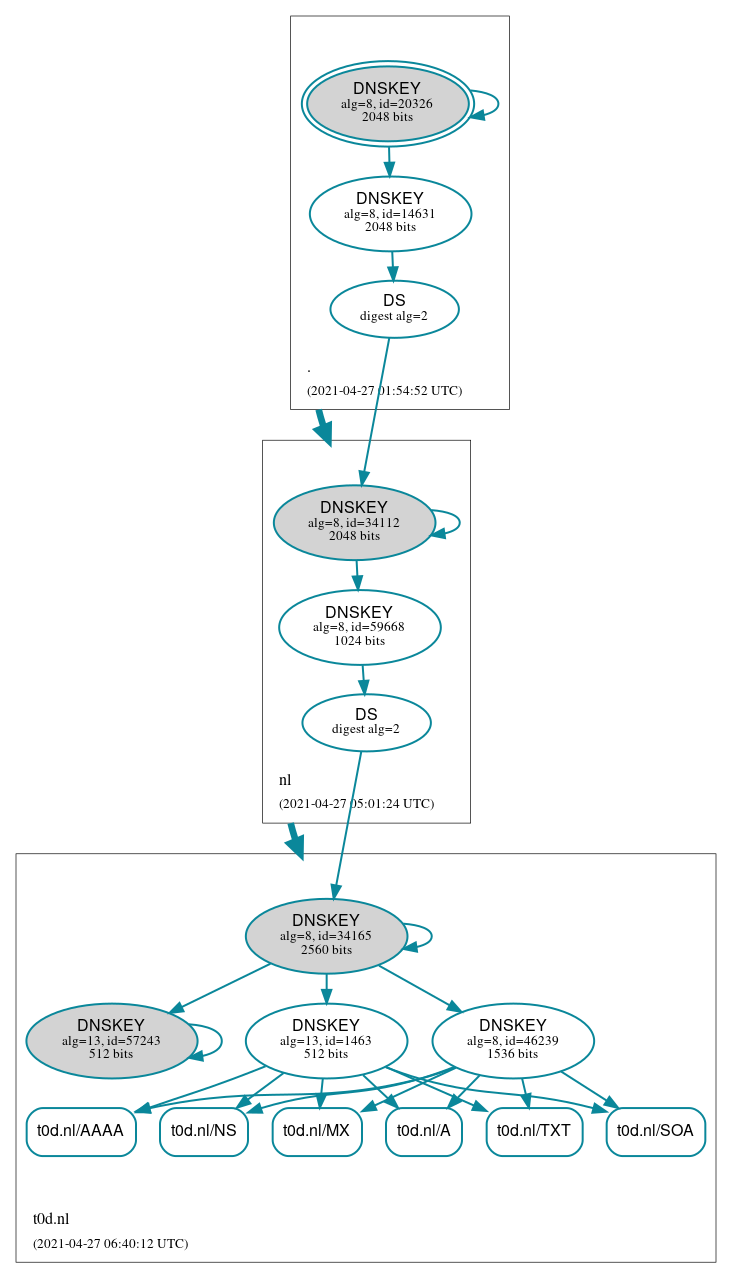
because the rest of internet have to get to know the new keys, we have to wait the max TTL of the zone (here 24h) before doing additional steps.
Add the DS-record to the parent
Then the DS-record has to be put in the parent zone. Depending on the zone, it has to be supplied in different ways to the registry.
[root@amys ~]# dnssec-dsfromkey -2 Kt0d.nl.+013+YYYYY
[root@amys ~]# cat Kt0d.nl.+013+YYYYY
After adding the DS-record information to the registrar, I checked that the new DS-record was available in the authoritive nameservers for the TLD.
[root@amys ~]# dig @ns1.dns.nl +short ds t0d.nl
When it was available in the authoritive nameserver, then I have to wait until the parent TTL to expire which is 1 hour (3600s) for .nl, 15m for .org and .net as can be checked by the following commands:
dig +multi @ns1.dns.nl soa nl
dig +multi @a0.org.afilias-nst.info. soa org
dig +multi @a.gtld-servers.net. soa net
After the TTL has passed you can see the two DS records in the parent:
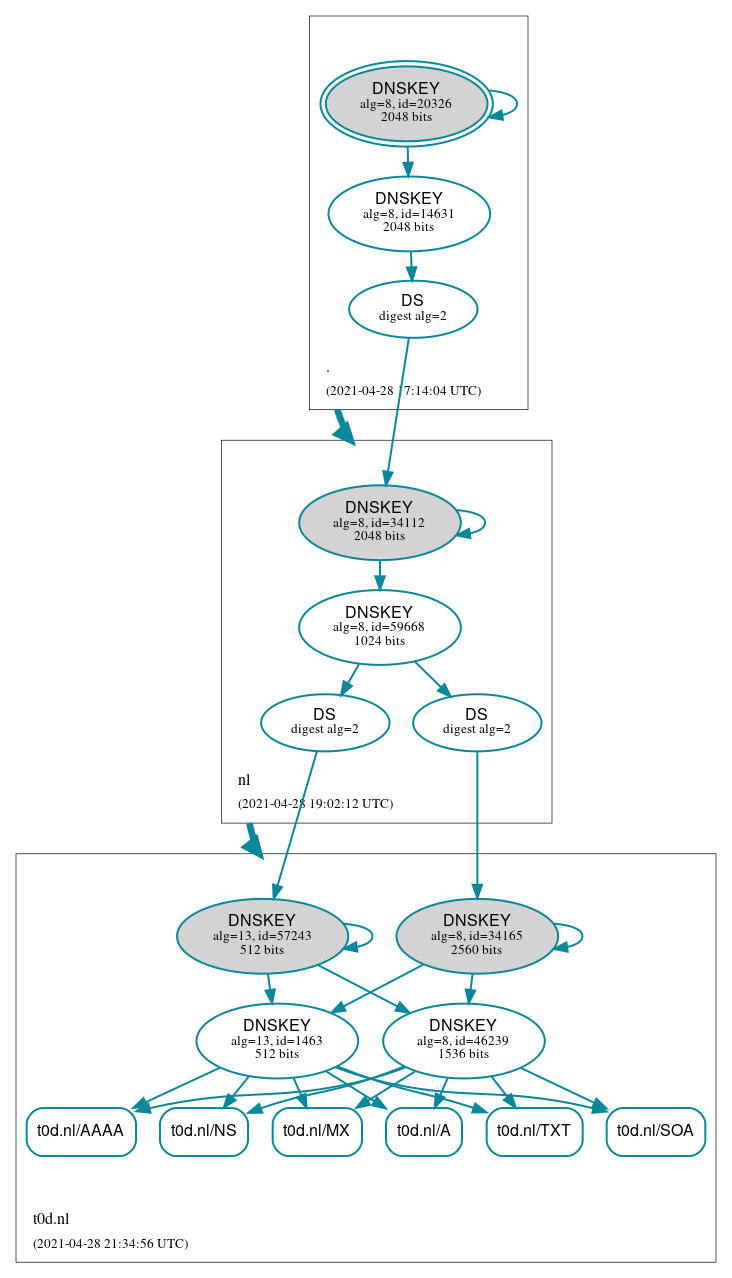
This corresponds with the following dnssec status in bind:
[root@amys ~]# rndc dnssec -status t0d.nl
dnssec-policy: rsa_to_ecdsa
current time: Wed Apr 28 18:11:33 2021
key: 57243 (ECDSAP256SHA256), KSK
published: yes - since Tue Apr 27 08:12:12 2021
key signing: yes - since Tue Apr 27 08:12:12 2021
No rollover scheduled
- goal: omnipresent
- dnskey: rumoured
- ds: hidden
- key rrsig: rumoured
key: 61968 (RSASHA256), ZSK
published: no
zone signing: no
Key has been removed from the zone
- goal: hidden
- dnskey: hidden
- zone rrsig: unretentive
key: 34165 (RSASHA256), KSK
published: yes - since Tue Sep 18 21:20:04 2018
key signing: yes - since Tue Sep 18 21:20:04 2018
No rollover scheduled
- goal: omnipresent
- dnskey: omnipresent
- ds: hidden
- key rrsig: omnipresent
key: 46239 (RSASHA256), ZSK
published: yes - since Sun Apr 25 21:12:27 2021
zone signing: yes - since Sun May 9 23:12:27 2021
Next rollover scheduled on Fri Jul 23 21:12:27 2021
- goal: omnipresent
- dnskey: rumoured
- zone rrsig: rumoured
key: 1463 (ECDSAP256SHA256), ZSK
published: yes - since Tue Apr 27 08:12:12 2021
zone signing: yes - since Tue Apr 27 08:12:12 2021
Next rollover scheduled on Sun Jul 11 06:12:12 2021
- goal: omnipresent
- dnskey: rumoured
- zone rrsig: rumoured
Inform bind that the DS-record is in the parent
Now I can tell bind that the DS-record record is in the parent.
[root@amys ~]# rndc dnssec -checkds -key 57243 published t0d.nl
KSK 57243: Marked DS as published since 29-Apr-2021 06:44:53.000
[root@amys ~]# rndc dnssec -status t0d.nl
dnssec-policy: rsa_to_ecdsa
current time: Thu Apr 29 06:45:16 2021
key: 57243 (ECDSAP256SHA256), KSK
published: yes - since Tue Apr 27 08:12:12 2021
key signing: yes - since Tue Apr 27 08:12:12 2021
No rollover scheduled
- goal: omnipresent
- dnskey: rumoured
- ds: hidden
- key rrsig: rumoured
key: 61968 (RSASHA256), ZSK
published: no
zone signing: no
Key has been removed from the zone
- goal: hidden
- dnskey: hidden
- zone rrsig: unretentive
key: 34165 (RSASHA256), KSK
published: yes - since Tue Sep 18 21:20:04 2018
key signing: yes - since Tue Sep 18 21:20:04 2018
No rollover scheduled
- goal: omnipresent
- dnskey: omnipresent
- ds: hidden
- key rrsig: omnipresent
key: 46239 (RSASHA256), ZSK
published: yes - since Sun Apr 25 21:12:27 2021
zone signing: yes - since Sun May 9 23:12:27 2021
Next rollover scheduled on Fri Jul 23 21:12:27 2021
- goal: omnipresent
- dnskey: rumoured
- zone rrsig: rumoured
key: 1463 (ECDSAP256SHA256), ZSK
published: yes - since Tue Apr 27 08:12:12 2021
zone signing: yes - since Tue Apr 27 08:12:12 2021
Next rollover scheduled on Sun Jul 11 06:12:12 2021
- goal: omnipresent
- dnskey: rumoured
- zone rrsig: rumoured
I still find it strange that the state of the key in rndc dnssec -status has not changed.
Now the old DS-record can be removed from the parent. Check when it has been removed.
[root@amys ~]# dig @ns1.dns.nl +short ds t0d.nl
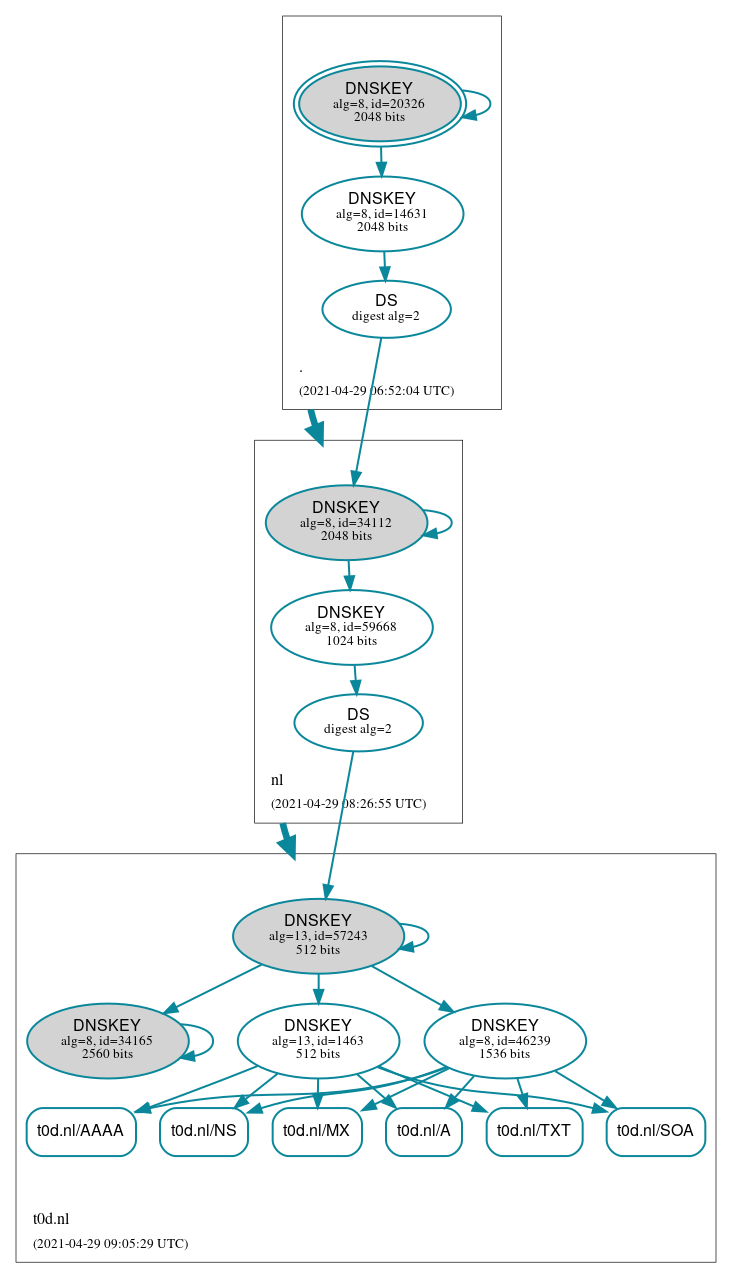
Change the policy
Now that the old DS-record has been removed, the policy can be changed to
ecdsa256_default.
zone "t0d.nl" {
type master;
dnssec-policy ecdsa256_default;
And after a rndc reload the old keys will no longer be in use.
[root@amys ~]# rndc dnssec -status t0d.nl
dnssec-policy: ecdsa256_default
current time: Thu Apr 29 11:17:18 2021
key: 57243 (ECDSAP256SHA256), KSK
published: yes - since Tue Apr 27 08:12:12 2021
key signing: yes - since Tue Apr 27 08:12:12 2021
No rollover scheduled
- goal: omnipresent
- dnskey: rumoured
- ds: hidden
- key rrsig: rumoured
key: 61968 (RSASHA256), ZSK
published: no
zone signing: no
Key has been removed from the zone
- goal: hidden
- dnskey: hidden
- zone rrsig: unretentive
key: 34165 (RSASHA256), KSK
published: no
key signing: no
Key has been removed from the zone
- goal: hidden
- dnskey: unretentive
- ds: hidden
- key rrsig: unretentive
key: 46239 (RSASHA256), ZSK
published: no
zone signing: no - scheduled Sun May 9 23:12:27 2021
Key has been removed from the zone
- goal: hidden
- dnskey: unretentive
- zone rrsig: unretentive
key: 1463 (ECDSAP256SHA256), ZSK
published: yes - since Tue Apr 27 08:12:12 2021
zone signing: yes - since Tue Apr 27 08:12:12 2021
Next rollover scheduled on Sun Jul 11 06:12:12 2021
- goal: omnipresent
- dnskey: rumoured
- zone rrsig: rumoured
After two hours I saw the following in the log.
29-Apr-2021 13:13:49.078 dnssec: info: zone t0d.nl/IN: reconfiguring zone keys
29-Apr-2021 13:13:49.206 dnssec: info: keymgr: retire DNSKEY t0d.nl/RSASHA256/61968 (ZSK)
29-Apr-2021 13:13:49.207 dnssec: info: keymgr: retire DNSKEY t0d.nl/RSASHA256/34165 (KSK)
29-Apr-2021 13:13:49.207 dnssec: info: keymgr: retire DNSKEY t0d.nl/RSASHA256/46239 (ZSK)
29-Apr-2021 13:13:49.254 dnssec: info: zone t0d.nl/IN: next key event: 30-Apr-2021 13:13:48.078
This is because the zone-propagation-delay in the policy is set to 2 hours.
After the TTL of the zone has passed the old keys are no longer visible to the world.
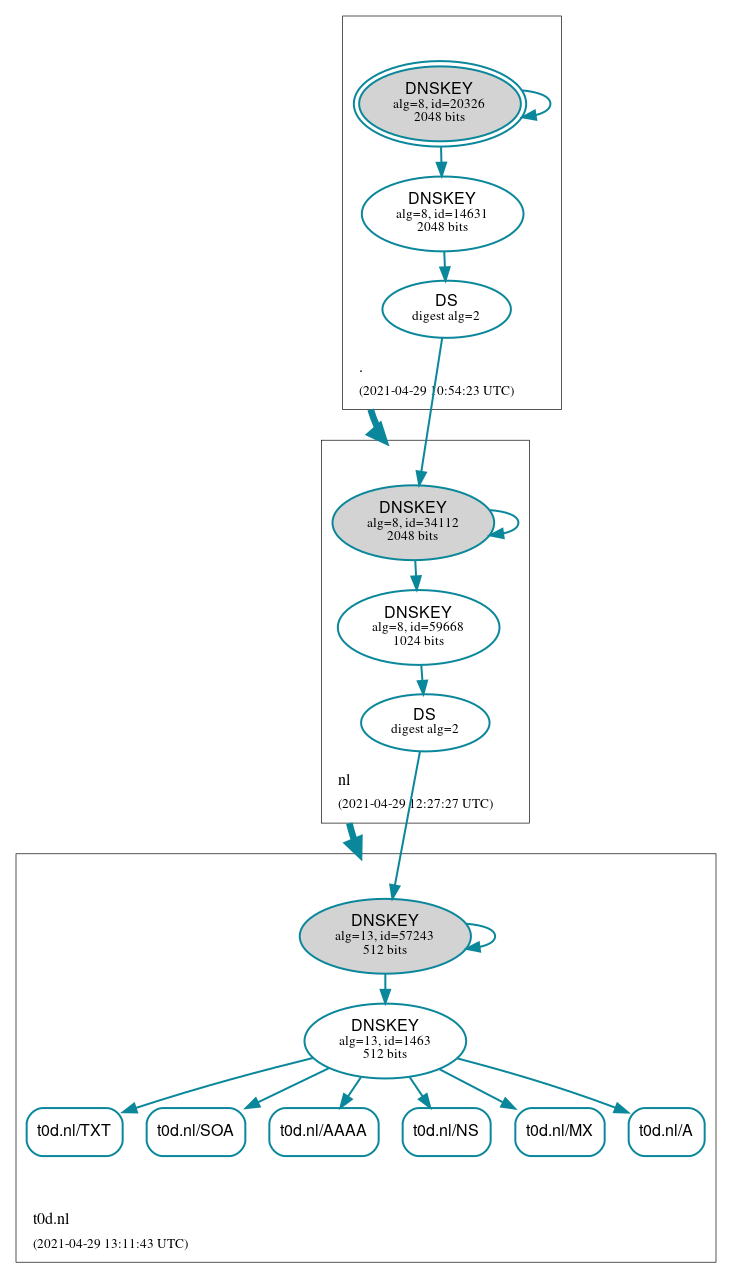
ZSK rollover
When a new ZSK is (automaticly) created it will be available for some time before it is used in signing.
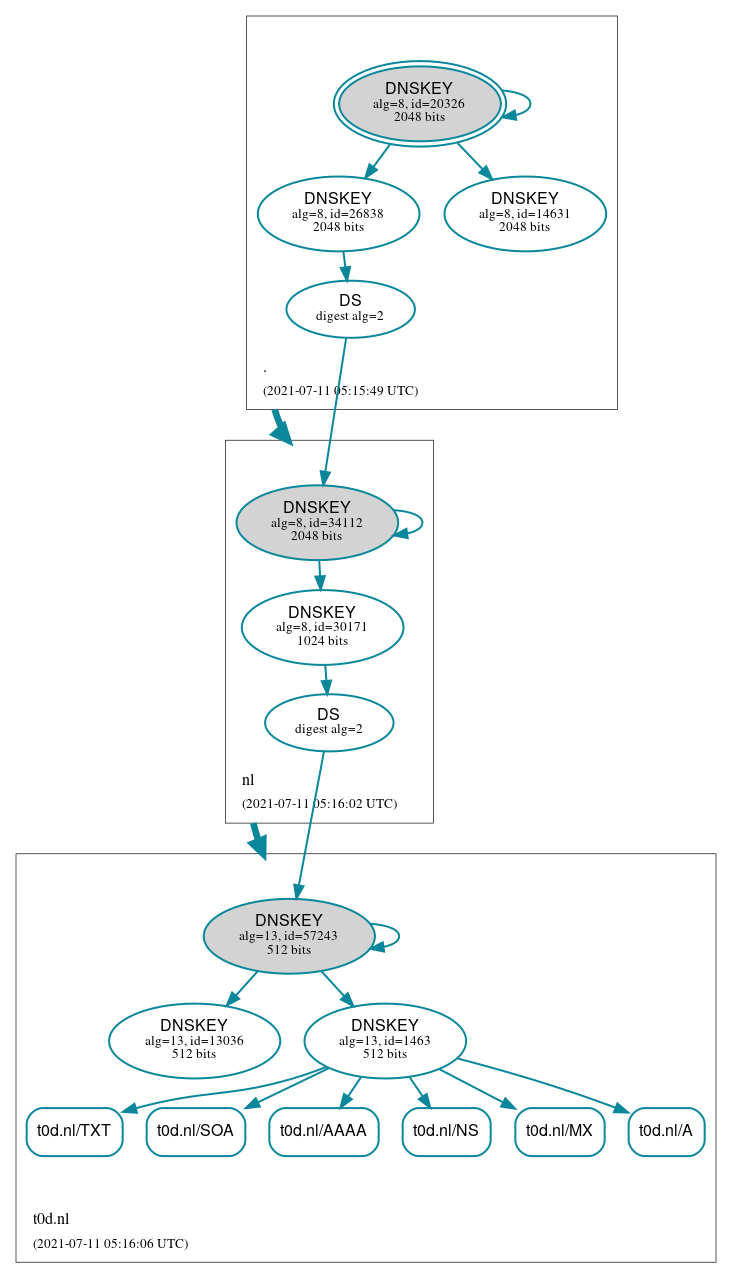
[root@amys ~]# rndc dnssec -status t0d.nl
dnssec-policy: ecdsa256_default
current time: Sun Jul 11 13:11:39 2021
key: 57243 (ECDSAP256SHA256), KSK
published: yes - since Tue Apr 27 08:12:12 2021
key signing: yes - since Tue Apr 27 08:12:12 2021
No rollover scheduled
- goal: omnipresent
- dnskey: omnipresent
- ds: omnipresent
- key rrsig: omnipresent
key: 13036 (ECDSAP256SHA256), ZSK
published: yes - since Sun Jul 11 06:12:12 2021
zone signing: no - scheduled Mon Jul 26 08:12:12 2021
Next rollover scheduled on Sat Oct 9 06:12:12 2021
- goal: omnipresent
- dnskey: rumoured
- zone rrsig: hidden
key: 1463 (ECDSAP256SHA256), ZSK
published: yes - since Tue Apr 27 08:12:12 2021
zone signing: yes - since Tue Apr 27 08:12:12 2021
Key will retire on Mon Jul 26 08:12:12 2021
- goal: hidden
- dnskey: omnipresent
- zone rrsig: omnipresent
Cleanup
If you still see old keys in the output, you can just (re)move the keys from the keys directory.
[root@amys bind]# mv keys/Kt0d.nl.+<3 digit algo number>+<key id>.* /tmp
When the ZSK rollover has been done, you can see a different state:
[root@amys ~]# rndc dnssec -status t0d.nl
dnssec-policy: ecdsa256_default
current time: Mon Jul 26 08:13:12 2021
key: 57243 (ECDSAP256SHA256), KSK
published: yes - since Tue Apr 27 08:12:12 2021
key signing: yes - since Tue Apr 27 08:12:12 2021
No rollover scheduled
- goal: omnipresent
- dnskey: omnipresent
- ds: omnipresent
- key rrsig: omnipresent
key: 13036 (ECDSAP256SHA256), ZSK
published: yes - since Sun Jul 11 06:12:12 2021
zone signing: yes - since Mon Jul 26 08:12:12 2021
Next rollover scheduled on Sat Oct 9 06:12:12 2021
- goal: omnipresent
- dnskey: omnipresent
- zone rrsig: rumoured
key: 1463 (ECDSAP256SHA256), ZSK
published: yes - since Tue Apr 27 08:12:12 2021
zone signing: no
Key is retired, will be removed on Thu Aug 19 11:12:12 2021
- goal: hidden
- dnskey: omnipresent
- zone rrsig: unretentive
Which is also seen in the world.
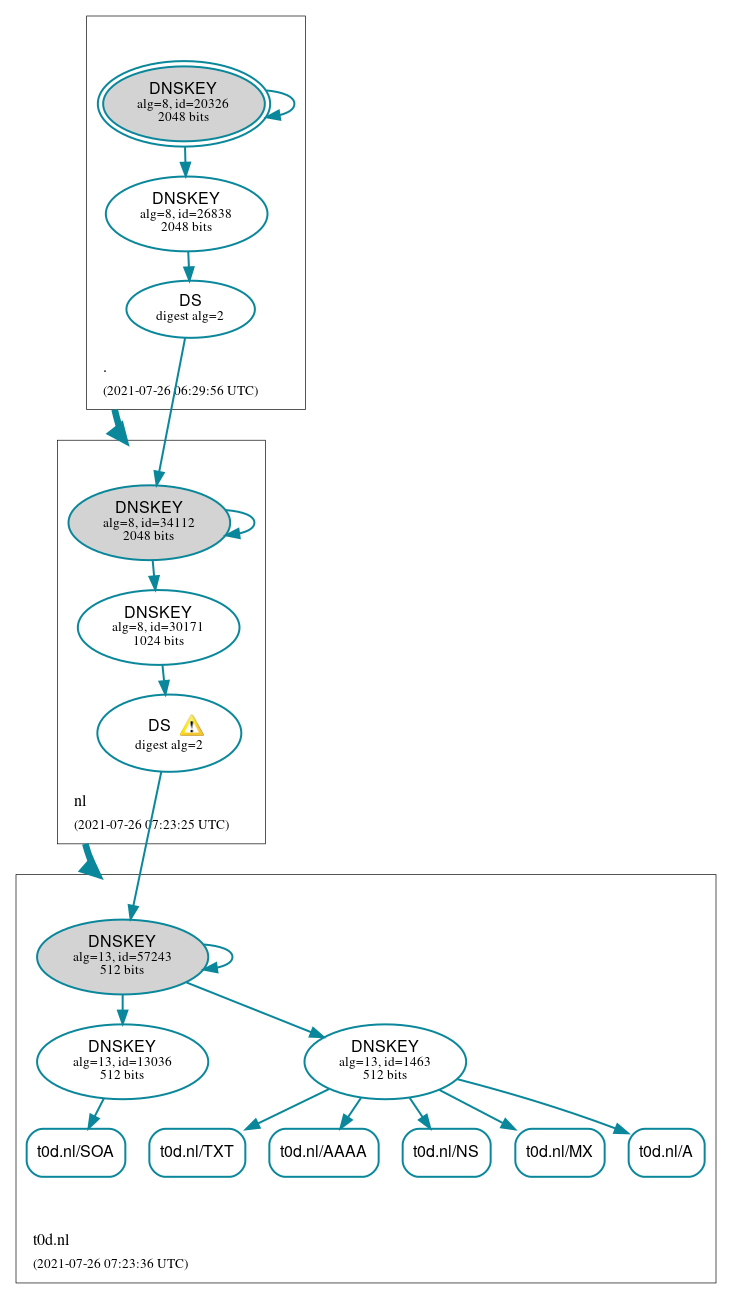
I had a lot of help from https://www.dns.cam.ac.uk/news/2020-01-15-rollover.html .