Why this item
When I was searching how to setup my new EdgeRouter Lite, I came across a link that would explain why using a zone based firewall is better than a per-interface firewall. Unfortually the webpage was no longer reachable, but at least google cache still had the text available. Because it is a good article, I put the text here as a backup. The original also has some pictures as can be seen by the archived page.
Per Interface vs. Zone Based Firewall
Every so often, I get asked the question of why I feel a Zone based firewall is better than a per-interface firewall. It can be a complicated question to answer depending on the asker’s level of understanding. So my goal here is to provide a simple and clear description of why a zone based firewall is the more secure solution.
In all firewall variants, we do matching against multiple attributes of a packet. Source IP, Source Port, Destination IP, Destination Port, session state, protocol and various other logical values depending on the implementation. The primary difference between ACLs and Zones are how they apply to the physical or layer 2 characteristics.
An ACL is a firewall rule that is applied to a sinlge interface for a specific direction of traffic such as inbound to eth0 or outbound on eth1. This means that only packets traveling in the specific direction for the specific interface will be matched regardless if any of the higher layer details match.
A Zone based firewall differs by instead of matching on the interface and direction it matches on the source and destination zones which translates to matching inbound on one interface and outbound on a second interface.
Side Note: Most zone based firewalls allow you to have multiple interfaces as members of a single zone. For example of you had a router with 4 interfaces and two of them you are using for a DMZ, you could add both DMZ interfaces to the DMZ zone and all rules which apply to that zone would apply to traffic on both of those interfaces.
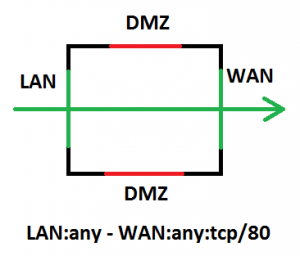
To try to illustrate the differences, consider a router with 4 interfaces and we want to allow traffic from the LAN to the WAN on tcp/80 for web traffic to the Internet.
To accomplish this with an ACL we could apply an inbound allow rule on the LAN interface such as:
allow LAN tcp/80 any
This would give us the following results since we only matched on the inbound interface and a destination of any could be on any of these interfaces.

Another alternative is to use an outbound ACL on the WAN interface.

This would give us the desired results but this is against best practices. By utilizing outbound rulesets a packet is able to traverse the majority of the firewall’s operations before it gets blocked. This uses more resources for a packet that will be dropped as well as creating a larger attack surface for vulnerabilities in the firewall itself.
The next option is to use multiple deny statements on your inbound interface to restrict traffic. For example:
allow LAN:any DMZ1:IP1:tcp/443
deny LAN:any DMZ1:any
deny LAN:any DMZ2:any
allow LAN:any any:tcp/80
deny any any
To implement inbound only ACLs you now add management complexities. Specific allows have to go above the internal deny statements. Generic allows have to go after the internal deny statements. While this is easy to manage when you only have a few rules, it doesn’t scale well when you get into hundreds of rules. It becomes very easy to make a mistake which opens your network wide open. Imagine adding an entry to your inbound LAN ACL which allows any destination above the internal deny statements. You would have just opened up your LAN to everything else. A compromised host would have unfettered access to everything in your network. If you have any regulatory security requirements, you would have just made a very big and potentially costly mistake because of a simple ordering issue.
allow LAN:any DMZ1:IP1:tcp/443
allow LAN:any any:tcp/443
deny LAN:any DMZ1:any
deny LAN:any DMZ2:any
allow LAN:any any:tcp/80
deny any any
With a Zone based firewall, it is much more difficult to make a mistake which will set your network wide open since you have to specify a source and destination zone for every rule. I have yet to see a firewall that will give you the option of any for the source or destination zone.
To implement this access, you would need only one rule to get the best results. Explicit allow on LAN and WAN with explicit deny on the DMZs.